Best Practices to Secure Your Code Signing Process

The code signing process is integral to any code and software development process. Individual and corporate developers need code signing certificates to safeguard software, drivers, application, and other executable scripts.
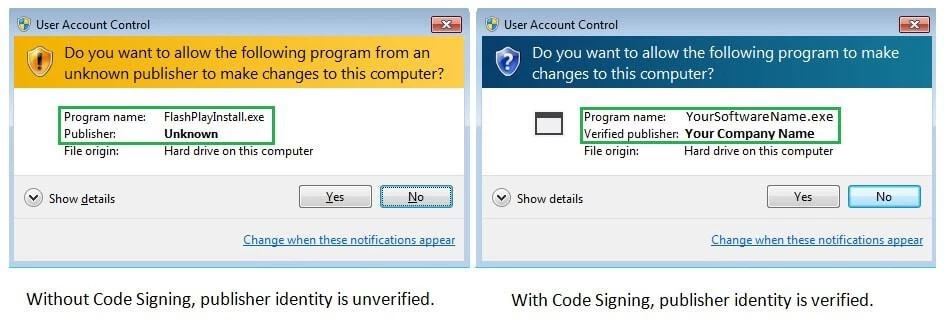
A cheap code signing certificate ensures ultimate users that a code has not been altered since it was signed.

Whereas the code signing process is pretty straightforward, specific security issues pertain to it. For instance, attackers have tried to steal private keys and use them to jeopardize an already-signed software or code. Therefore, securing the entire code signing process is a great idea.
The big question is how to go about securing the code signing process. In this article, I will be glad to walk you through some of the best practices you should adopt to secure your code signing process.
7 Practices For Secure Code Signing
Below are some of the best code signing security practices you should implement for the secure code signing process.
1. Minimize and Control Access to Private Keys
One of the most rampant security hacks associated with code signing certificates is when hackers steal, exfiltrate or compromise your private keys. The fact that it is possible to sign a code from anywhere is quite alluring to hackers who get the freedom to steal private keys from anywhere, as long as they have the proper infrastructure, time, and technical know-how to do it.
Malicious actors who succeed in stealing private keys usually offer them for sale on the dark web. Moreover, it is interesting to learn that some private keys are priced higher than guns and drugs. This should give you a fair picture of the demand for private keys.
To avoid losing private keys to malicious actors, you must begin minimizing and controlling access to private keys. Here is how you can achieve that:
- Grant access of private keys to the minimum number of computers
- Only authorized personnel, such as developers who have business with private keys, should be allowed to access them.
- Enhance proper physical security measures to ensure that no unauthorized personnel can access critical infrastructure carrying private keys.
2. Store Your Private Keys in a Centralized and Safe Space
Another best practice for securing your code signing process is storing your private keys in safe and centralized spaces. A centralized space will keep your keys from unsafe alterations by unauthorized parties.
Moreover, it would be best if you utilized devices whose safety has been proven to store private keys. These devices should remain under constant watch to keep infiltrators at bay. Doing so will eliminate any attempts made by malicious actors to steal private keys and hamper the security of your code signing process.
3. Leverage Strong Passwords and Cryptographic Hardware
Any subject involving cybersecurity is incomplete without the mention of strong passwords. Using a solid sixteen-character password and cryptographic hardware is one of the best approaches to protect the private keys of your executables.
A strong, complex, unique password is essential, especially when transporting private keys between devices or sharing them via email.
A good password for securing your private keys should be randomly generated. The password should blend numbers, letters, and special characters. Such a password is strong enough to withstand automated brute-force attacks and manual guesses.
In addition to strong and unique passwords, it is also wise to use cryptographic hardware to strengthen your private key protection plan further. Cryptographic hardware that employs the latest encryption algorithms to secure your code signing certificate is also a vital protection plan.
With these algorithms, unauthorized parties cannot access code signing certificate keys. Cryptographic hardware devices also do not allow the exportation of private keys. They also require two-factor authentication, and this further boosts the security of your code signing process.
4. Be Mindful of the Code Signing Certificate You Choose for Your Code
It is also vital to ensure you acquire your code signing certificate from a trusted certificate authority. You can consider two types of code signing certificates for your code signing process.
Corporate developers usually use Organization Validation (OV) code signing certificates for digitally signing their software. The OV code signing certificate will eliminate publisher warnings and showcase your identity by displaying your name.
You can also consider working with EV code signing certificate, which requires higher authentication of the publisher or organization and comes with a Microsoft Smart Screen Filter.
You must take keen note of the certificate authority you pick for your code signing certificate needs. Not all certificate authorities can be trusted.
It is recommended to work with a globally trusted CA such as a DigiCert Code Signing certificate, Comodo Code Signing certificate, Sectigo Code Signing Certificate.
All these certs are genuine and come at a pocket-friendly price.
5. Thoroughly Scan Your Code for Bugs
This is a crucial step that you should apply before beginning your code-signing process. Scanning your code helps you ascertain that the code is secure and does not carry bugs that could potentially bring severe harm to your applications or software.
You should prompt your security team to frequently review your software code for any threats before you can proceed with the code signing process. All detected bugs should be fixed immediately.
In short, you must undertake robust QA testing to resolve all bugs and issues that could compromise your certificate signing process.
6. Code Authentication
You should make code authentication an integral part of your software development lifecycle. You should ensure that all codes are authenticated before they are released.
It would be best if you established a separate process for approving codes before signing them. Doing so will help protect you from signing malicious and unapproved codes.
In short, the code authentication process will help to establish whether your codes are worthy and ready to be signed.
7. Revoke All Compromised Code Signing Certificates
If you notice that your private keys have been compromised, you should act fast and report the issue to your certificate authority. The certificate authority will then proceed to revoke the certificates.
If you have already time-stamped your code signing certificate, you should select the revocation date before the date the code was compromised to show that the certificate was not impacted.
Final Words
One of the best ways to secure your codes, software, applications, and executables is by using a code signing certificate. The certificate guarantees that the code has not been compromised since it was signed.
However, a secure code signing process is required for every publisher or developer. This article has explained a few practices you can follow to secure the process.
You may also read: Tips for Learning Java at University




